- By Vikas Yadav
- Sun, 04 Feb 2024 07:40 PM (IST)
- Source:JND
Vision Pro headset was made available by Apple at its flagship stores in the United States on February 2. And hours after offline availability, a PhD student of Massachusetts Institute of Technology (MIT) has reportedly discovered a kernel exploit for the headset's software - visionOS. If the claims are to be believed, this can open gates for the creation of jailbreak and malicious software for the device in the future, according to AppleInsider.
It is similar to a movement of malware creators and security experts to discover the flaws in the initial builds of any popular software system. Something similar to the attempts to jailbreak an iOS device. In the latest instance, Joseph Ravichandran, a student of Microarchitectural Security at MIT, posted (on X (formerly Twitter)) about a possible first kernel exploit for the Vision Pro headset.
Also Read: Apple Vision Pro: Fans To Motors, Check What's Inside The Spatial Computer | Teardown
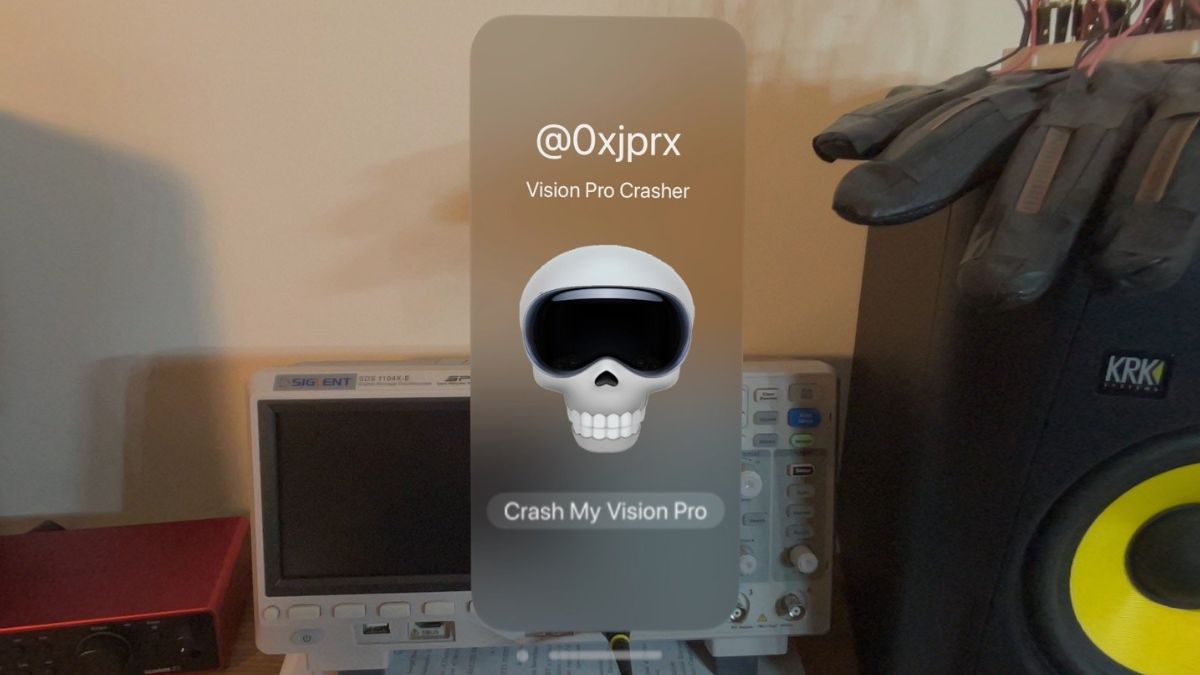
Once the kernel exploit is tested, the Vision Pro crashes and "switches to full passthrough and displays a warning to remove the device in 30 seconds so it can reboot." After the rebooting is complete, the panic log indicates that the kernel crashed, the report added. In another photo posted by the user, the "Vision Pro Crasher" app is visible with a 3D skull icon wearing the headset and a button with text: "Crash My Vision Pro".
When the device crashes it switches to full passthrough and displays a warning to remove the device in 30 seconds so it can reboot. Pretty cool pic.twitter.com/f4KYxSiVsq
— Joseph Ravichandran (@0xjprx) February 3, 2024
It is not clear whether the researcher plans to submit the findings (or has submitted) the discoveries to the Cupertino-based tech giant. Depending on the severity, these findings may qualify for the company's Security Bounty program. If the exploit gets pushed to Apple's notice, the company will likely issue a fix swiftly due to the premium nature of the device.
However, due to the skewed number of purchases in the initial stages, the impact of this exploit may remain limited in the short run. Such kernel exploits are among the key elements in jailbreaking a device that helps perform actions otherwise restricted in the software. It can include installing malicious programs, revising the UI design, and unlocking other core functionalities, according to iDownloadBlog. However, this will require several other breaching measures within the OS.